Computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development.Wikipedia
- OSSIM
Open source security information and event management system, integrating a selection of tools designed to aid network administrators in computer security, intrusion detection and prevention. The project began in 2003 as a collaboration between Dominique Karg, Julio Casal and later Alberto Román.Wikipedia
- Norton Internet Security
Computer program that provides malware prevention and removal during a subscription period and uses signatures and heuristics to identify viruses. Other features included in the product are a personal firewall, email spam filtering, and phishing protection.Wikipedia
- ZMap (software)
Free and open-source security scanner that was developed as a faster alternative to Nmap. Designed for information security research and it can be used for both white hat and black hat purposes.Wikipedia
- Network Security Toolkit
Linux-based Live DVD/USB Flash Drive that provides a set of free and open-source computer security and networking tools to perform routine security and networking diagnostic and monitoring tasks. The distribution can be used as a network security analysis, validation and monitoring tool on servers hosting virtual machines.Wikipedia
- OpenVAS
Software framework of several services and tools offering vulnerability scanning and vulnerability management. All OpenVAS products are free software, and most components are licensed under the GNU General Public License (GPL).Wikipedia
- Splint (programming tool)
Programming tool for statically checking C programs for security vulnerabilities and coding mistakes. Modern version of the Unix lint tool.Wikipedia
- ArpON
Computer software project to improve network security. Frequently cited as a means of protecting against ARP-based attacks.Wikipedia
- Yasca
Open source program which looks for security vulnerabilities, code-quality, performance, and conformance to best practices in program source code. It leverages external open source programs, such as FindBugs, PMD, JLint, JavaScript Lint, PHPLint, Cppcheck, ClamAV, Pixy, and RATS to scan specific file types, and also contains many custom scanners developed for Yasca.Wikipedia
- RIPS
Static code analysis software for the automated detection of security vulnerabilities in PHP and Java applications. Written by Johannes Dahse and released during the Month of PHP Security in May 2010 as open-source software.Wikipedia
- Burp Suite
Graphical tool for testing Web application security. Written in Java and developed by PortSwigger Web Security.Wikipedia
- OpenSSH
Suite of secure networking utilities based on the Secure Shell (SSH) protocol, which provides a secure channel over an unsecured network in a client–server architecture. OpenSSH started as a fork of the free SSH program developed by Tatu Ylönen; later versions of Ylönen's SSH were proprietary software offered by SSH Communications Security.Wikipedia
- Lynis
Extensible security audit tool for computer systems running Linux, FreeBSD, macOS, OpenBSD, Solaris, and other Unix-derivatives. It assists system administrators and security professionals with scanning a system and its security defenses, with the final goal being system hardening.Wikipedia
- Eclipse (software)
Integrated development environment used in computer programming. Extensible plug-in system for customizing the environment.Wikipedia
- W3af
Open-source web application security scanner. The project provides a vulnerability scanner and exploitation tool for Web applications.Wikipedia
- SonarQube
Open-source platform developed by SonarSource for continuous inspection of code quality to perform automatic reviews with static analysis of code to detect bugs, code smells, and security vulnerabilities on 20+ programming languages. SonarQube offers reports on duplicated code, coding standards, unit tests, code coverage, code complexity, comments, bugs, and security vulnerabilities.Wikipedia
- Parasoft C/C++test
Integrated set of tools for testing C and C++ source code that software developers use to analyze, test, find defects, and measure the quality and security of their applications. It supports software development practices that are part of development testing, including static code analysis, dynamic code analysis, unit test case generation and execution, code coverage analysis, regression testing, runtime error detection, requirements traceability, and code review.Wikipedia
- Java (software platform)
Set of computer software and specifications developed by James Gosling at Sun Microsystems, which was later acquired by the Oracle Corporation, that provides a system for developing application software and deploying it in a cross-platform computing environment. Used in a wide variety of computing platforms from embedded devices and mobile phones to enterprise servers and supercomputers.Wikipedia
- Symantec Endpoint Protection
Security software suite, which consists of anti-malware, intrusion prevention and firewall features for server and desktop computers. It has the largest market-share of any product for endpoint security.Wikipedia
- OpenSSL
Software library for applications that secure communications over computer networks against eavesdropping or need to identify the party at the other end. Widely used by Internet servers, including the majority of HTTPS websites.Wikipedia
- MPack (software)
PHP-based malware kit produced by Russian crackers. Released in December 2006.Wikipedia
- IntelliJ IDEA
Integrated development environment written in Java for developing computer software. Developed by JetBrains , and is available as an Apache 2 Licensed community edition, and in a proprietary commercial edition.Wikipedia
- Security Vision
Security Vision – software meant for automation of information security management system (ISMS) organisation. Representative of security operations center .Wikipedia
- Nessus (software)
Proprietary vulnerability scanner developed by Tenable, Inc. Examples of vulnerabilities and exposures Nessus can scan for include:Wikipedia
- Openswan
In the field of computer security, Openswan provides a complete IPsec implementation for Linux 2.0, 2.2, 2.4 and 2.6 kernels. Openswan, begun as a fork of the now-defunct FreeS/WAN project, continues to use the GNU General Public License.Wikipedia
- Sguil
Collection of free software components for Network Security Monitoring (NSM) and event driven analysis of IDS alerts. Written in Tcl/Tk and can be run on any operating system that supports these.Wikipedia
- Network Security Services
In computing, Network Security Services (NSS) comprises a set of libraries designed to support cross-platform development of security-enabled client and server applications with optional support for hardware TLS/SSL acceleration on the server side and hardware smart cards on the client side. NSS provides a complete open-source implementation of cryptographic libraries supporting Transport Layer Security (TLS) / Secure Sockets Layer (SSL) and S/MIME.Wikipedia
- LibreSSL
Open-source implementation of the Transport Layer Security protocol. Named after Secure Sockets Layer , the deprecated predecessor of TLS, for which support was removed in release 2.3.0.Wikipedia
- Armitage (computing)
Graphical cyber attack management tool for the Metasploit Project that visualizes targets and recommends exploits. Free and open source network security tool notable for its contributions to red team collaboration allowing for: shared sessions, data, and communication through a single Metasploit instance.Wikipedia
- Pure-FTPd
Free FTP Server with a strong focus on software security. It can be compiled and run on a variety of Unix-like computer operating systems including Linux, OpenBSD, NetBSD, FreeBSD, DragonFly BSD, Solaris, Tru64, Darwin, Irix and HP-UX.Wikipedia
- PHP Development Tools
Language IDE plugin for the Eclipse platform and the open-source project that develops it. The project intends to encompass all tools necessary to develop PHP based software.Wikipedia
Sentences forMetasploit Project
- On 2 July 2013, Rapid7 published a guide to security penetration testing of the latest IPMI 2.0 protocol and implementations by various vendors.Intelligent Platform Management Interface-Wikipedia
- For example, Metasploit can be used in many cases to obtain credentials from one machine which can be used to gain control of another machine.NT LAN Manager-Wikipedia
- Rapid7 notice that DMCA adversely affects good faith security research by forbidding researchers from circumventing technological protection measures (TPMs) to analyze software for vulnerabilities.Digital Millennium Copyright Act-Wikipedia
- The Internet Explorer exploit code used in the attack has been released into the public domain, and has been incorporated into the Metasploit Framework penetration testing tool.Operation Aurora-Wikipedia
- The Metasploit Project, for example, maintains a database of suitable opcodes, though it lists only those found in the Windows operating system.Buffer overflow-Wikipedia
- On 6 September 2019, a Metasploit exploit of the wormable BlueKeep security vulnerability was announced to have been released into the public realm.BlueKeep-Wikipedia
Proftpd Vs Pure Ftpd
- In February 2013, a vulnerability with the webarchive format was discovered and reported by Joe Vennix, a Metasploit Project developer.Webarchive-Wikipedia
- It is a supported platform of the Metasploit Project's Metasploit Framework, a tool for developing and executing security exploits.Kali Linux-Wikipedia
- In July 2010, w3af announced its sponsorship and partnership with Rapid7.W3af-Wikipedia
- The phrase has been adopted by the Metasploit framework as the name of a polymorphic XOR additive feedback encoder for X86 shellcode.Shikata ga nai-Wikipedia
- One of the more well known tools that is often used for data hiding is called Slacker (part of the Metasploit framework).Anti-computer forensics-Wikipedia
- As reported by The Tech Herald in August 2010, 'Google, Microsoft, TippingPoint, and Rapid7 have recently issued guidelines and statements addressing how they will deal with disclosure going forward.'Vulnerability (computing)-Wikipedia
- A month later, the company announced it would partner with SecureWorks, Ernst & Young, Kroll, Trustwave, and Rapid7 to provide managed security and incident response services.Carbon Black (company)-Wikipedia
- One of the more widely known trail obfuscation tools is Timestomp (part of the Metasploit Framework).Anti-computer forensics-Wikipedia
- He served as chief research officer at Boston, Massachusetts-based security firm Rapid7, a provider of security data and analytics software and cloud solutions.H. D. Moore-Wikipedia
- Marcus Carey, a security researcher for Rapid7, said that the hackers had penetrated the databases of LinkedIn in the preceding days.2012 LinkedIn hack-Wikipedia
- Since leaving Rapid7, Moore has joined Atredis Partners as the vice president of research and development and founded Critical Research Corporation, the software firm that develops Rumble Network Discovery.H. D. Moore-Wikipedia
- While technical implementation of these attacks may be challenging due to cross-browser incompatibilities, a number of tools such as BeEF or Metasploit Project offer almost fully automated exploitation of clients on vulnerable websites.Clickjacking-Wikipedia
- The project has also stated that binary drivers 'hide bugs and workarounds for bugs', an observation which has been somewhat vindicated by flaws found in binary drivers (including an exploitable bug in Nvidia's 3D drivers discovered in October 2006 by Rapid7).Free and open-source graphics device driver-Wikipedia
- Such programs have included remote denial-of-service WinNuke, trojans, Back Orifice, NetBus and Sub7 vulnerability scanner/injector kit Metasploit and often software intended for legitimate security auditing.Script kiddie-Wikipedia
- He is a developer of the Metasploit Framework, a penetration testing software suite, and the founder of the Metasploit Project.H. D. Moore-Wikipedia
- Microsoft developers were visibly uncomfortable when Metasploit was demonstrated.BlueHat-Wikipedia
- They were made available as open sourced Metasploit modules.EternalBlue-Wikipedia
- Armitage is a graphical cyber attack management tool for the Metasploit Project that visualizes targets and recommends exploits.Armitage (computing)-Wikipedia
- Armitage is a GUI front-end for the Metasploit Framework developed by Raphael Mudge with the goal of helping security professionals better understand hacking and to help them realize the power of Metasploit.Armitage (computing)-Wikipedia
- Radare2 can also assist in creating shellcodes with its 'ragg2' tool, similar to metasploit.Radare2-Wikipedia
- It is a free and open source network security tool notable for its contributions to red team collaboration allowing for: shared sessions, data, and communication through a single Metasploit instance.Armitage (computing)-Wikipedia
- WarVox was merged into the Metasploit Project in August 2011.WarVOX-Wikipedia
- The 'most epic fail' award was presented by Metasploit creator HD Moore to F5 Networks for their static root SSH key issue, and the award was accepted by an employee of F5, unusual because the winner of this category usually does not accept the award at the ceremony.Pwnie Awards-Wikipedia
- Finjan has filed a large number of lawsuits against leading software security companies asserting its patents including against: Cisco, Palo Alto Networks, Symantec, Blue Coat Systems, Sophos, Trend Micro, ESET, Bitdefender, Check Point, Qualys, Rapid7, Fortinet and others.Finjan-Wikipedia
This will create an email alert. Stay up to date on result for: Metasploit Project
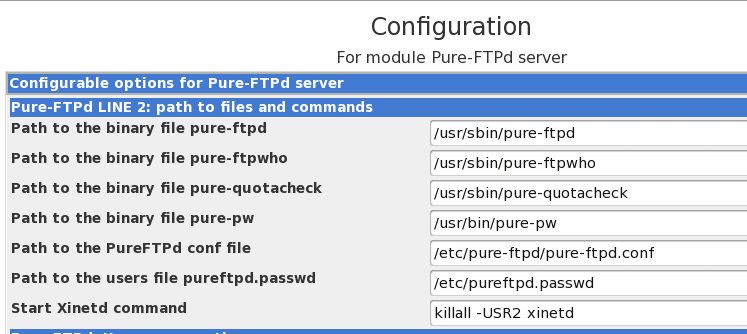
Pure Ftpd Configuration
Pure-pw useradd samiux -u ftpuser -d /ftphome/ pure-pw mkdb. 'pure-pw mkdb' should be issued when a new user is added. Make sure you have a directory /ftphome. Step 9: Add TLS/SSL support and generate a private certificate: cd /etc/pure-ftpd/conf/ echo 1 TLS openssl req -x509 -nodes -newkey rsa:1024 -keyout /etc/ssl/private/pure-ftpd.
Pure Ftpd Exploit
Before install your FTP Server: kali box Setting Pure-FTPD #apt-get install pure-ftpd #cat setup-ftp #groupadd ftpgroup #useradd -g ftpgroup -d /dev/null -s /etc ftpuser #pure-pw useradd offsec -u ftpuser -d /ftphome #pure-pw mkdb #cd /etc/pure-ftpd/auth/ #ln -s./conf/PureDB 60pdb #mkdir -p /ftphome #chown -R ftpuser:ftpgroup /ftphome/ #/etc/init.d/pure-ftpd restart execute setup-ftp Execute. Pure-FTPd - External Authentication Bash Environment Variable Code Injection (Metasploit). Ok, there are plenty of services just waiting for our attention. So let’s check each port and see what we get. There is an exploit available in Metasploit for the vsftpd version. FTP/S (TCP/990) TLDR. WHAT IT IS: FTP, but with an SSL wrapper, much like HTTPS is merely HTTP with an SSL layer. HOW MANY: 459,907 discovered nodes. 84,607 (18%) have Recog fingerprints (10 total service families).




